Threat Watch
Instantly uncover your cyber security health with Threat Watch's actionable insights into compromised accounts and de...
Visit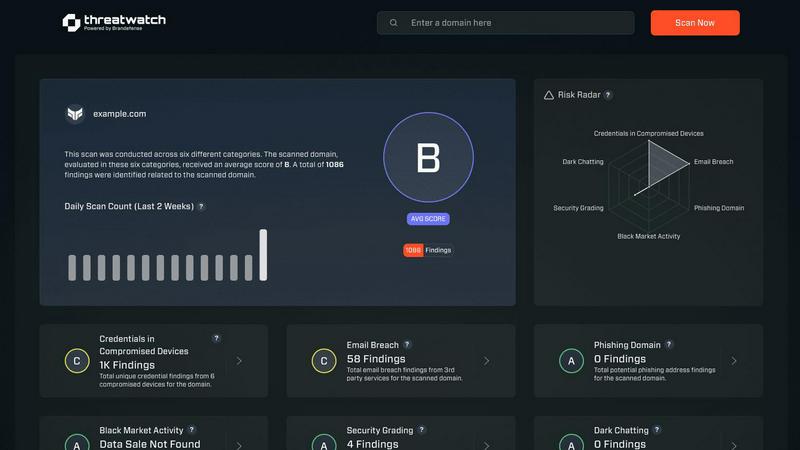
About Threat Watch
Threat Watch is a cutting-edge cybersecurity intelligence solution designed to empower organizations in understanding and managing their cyber health. It meticulously evaluates an array of critical security categories, including compromised credentials, breached accounts, phishing addresses, and dark web content. By providing a unified view of an organization’s assets, vulnerabilities, and exposures, Threat Watch enables businesses to swiftly identify and prioritize risks. This tool is essential for IT professionals, security teams, and business leaders who are dedicated to safeguarding their digital environment. With real-time insights and automated assessments, Threat Watch transforms complex data into actionable intelligence, allowing organizations to mitigate risks faster and more effectively than ever before. Discover your cybersecurity health and fortify your defenses with Threat Watch.
Features of Threat Watch
Real-Time Insights
Stay ahead of potential threats with real-time insights that keep you informed about vulnerabilities in your organization. This feature enables you to receive immediate alerts about possible breaches, allowing for rapid response and remediation.
Automated Assessments
Threat Watch utilizes automated assessments to evaluate your organization's cybersecurity posture continuously. This feature minimizes manual effort while ensuring that your defenses are always up-to-date, providing peace of mind and efficiency.
Comprehensive Security Evaluation
Gain a holistic view of your cybersecurity landscape with a comprehensive evaluation of critical security categories. This feature helps organizations identify weaknesses and strengths, facilitating informed decision-making for risk management.
Dark Web Monitoring
Stay vigilant against cyber threats with dark web monitoring that alerts you to compromised credentials and sensitive information. This feature helps you take proactive measures to protect your organization from potential breaches and identity theft.
Use Cases of Threat Watch
Incident Response
In the event of a security incident, Threat Watch can be your first line of defense. By quickly identifying compromised accounts and vulnerabilities, organizations can respond with precision and minimize potential damage.
Risk Management
Organizations can leverage Threat Watch to enhance their risk management strategies. With detailed reports on vulnerabilities and exposures, security teams can prioritize remediation efforts based on the most significant risks to the organization.
Compliance Assurance
For businesses needing to comply with regulatory standards, Threat Watch provides essential insights into cybersecurity health. This tool assists in ensuring that security practices meet compliance requirements, reducing the risk of penalties.
Employee Training and Awareness
Threat Watch can be instrumental in developing employee training programs. By identifying common phishing addresses and potential threats, organizations can educate staff on recognizing and avoiding security risks effectively.
Frequently Asked Questions
What types of organizations can benefit from Threat Watch?
Threat Watch is designed for a wide range of organizations, from small businesses to large enterprises. Any entity looking to enhance its cybersecurity posture and gain insights into vulnerabilities can greatly benefit from this solution.
How does Threat Watch keep my data secure?
Threat Watch employs advanced encryption methods and secure protocols to ensure that all data processed and stored is protected. This commitment to security helps maintain the confidentiality and integrity of your organization's information.
Can Threat Watch integrate with existing security tools?
Yes, Threat Watch is designed to be compatible with various existing security tools and platforms. This integration capability allows organizations to enhance their current security measures without disrupting established workflows.
How often does Threat Watch conduct assessments?
Threat Watch conducts assessments continuously, providing organizations with real-time updates on their cybersecurity health. This proactive approach ensures that any emerging threats are identified and addressed promptly.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
aVenture
aVenture is your gateway to uncovering private company insights, tracking investors, and navigating the startup lands...
iGPT
iGPT gives enterprise agents secure, instant answers from messy email data and attachments.