Binary Vulnerability Analysis
About Binary Vulnerability Analysis
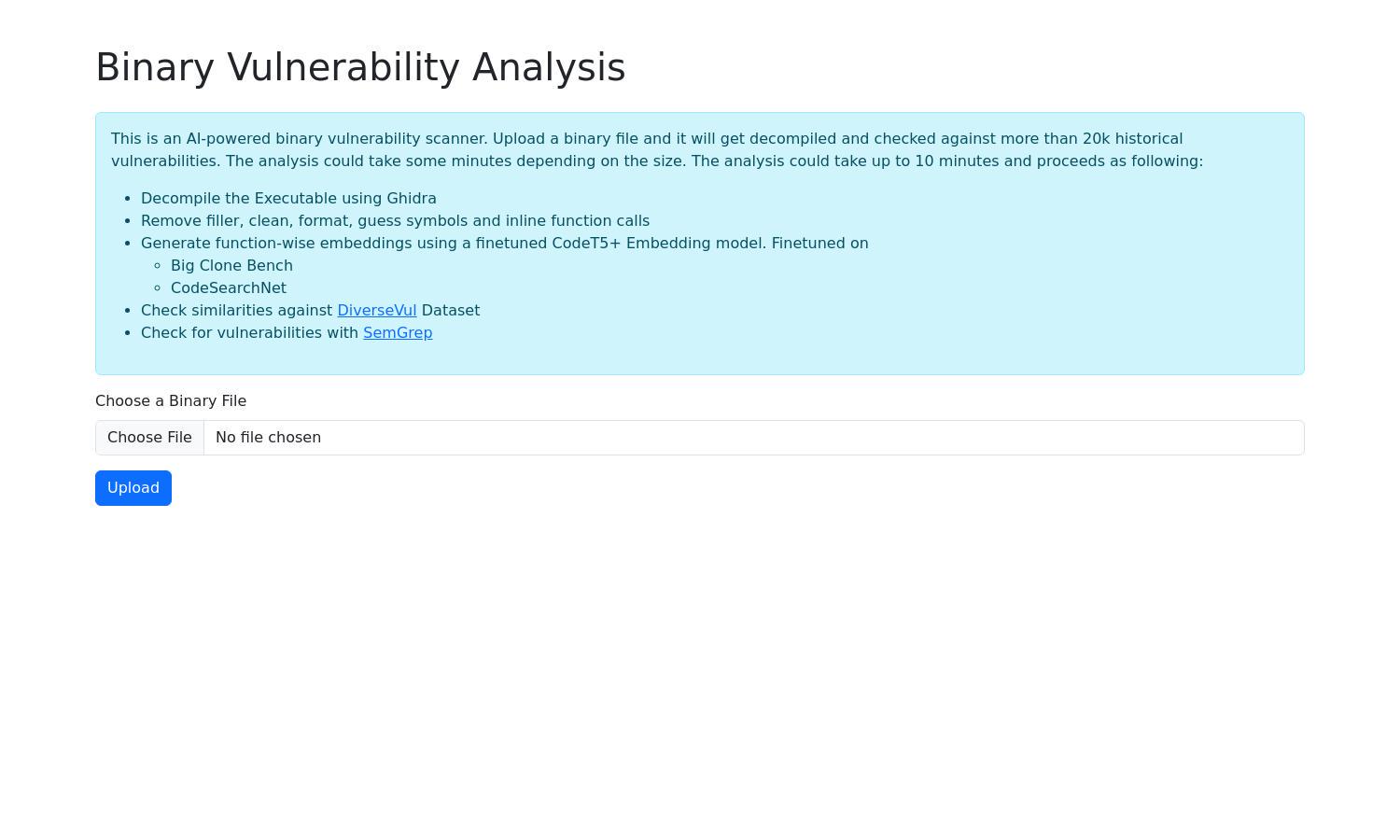
Binary Vulnerability Analysis empowers developers by providing an AI-driven binary vulnerability scanner. Users upload their binary files, which are decompiled using advanced tools like Ghidra, subsequently analyzed against a vast database of historical vulnerabilities. This innovative system enhances software security and ensures the integrity of executable files.
Binary Vulnerability Analysis offers flexible pricing plans tailored to various user needs. The foundational tier provides essential scanning features, while premium plans unlock advanced analysis capabilities and faster processing times. Special discounts are available for long-term subscriptions, enhancing software security for all users at competitive rates.
Binary Vulnerability Analysis features a user-friendly interface designed for seamless interactions. Its intuitive layout guides users through the scanning process, making it easy to upload and analyze binary files. Unique features enhance user experience while navigating through vulnerability reports, ensuring clarity and efficiency throughout.
How Binary Vulnerability Analysis works
Users start with Binary Vulnerability Analysis by registering on the web platform. After onboarding, they can easily upload a binary file for analysis. The system harnesses AI and advanced decompilation techniques, checking the file against historical vulnerabilities within minutes. Users receive comprehensive reports detailing any issues found, facilitating informed decision-making regarding security improvements.
Key Features for Binary Vulnerability Analysis
AI-Powered Vulnerability Scanning
Binary Vulnerability Analysis utilizes advanced AI technology to conduct vulnerability scans on uploaded binaries. This unique feature ensures that even intricate vulnerabilities are detected, offering users peace of mind about their software security. The system's efficiency and accuracy make it invaluable for developers seeking robust protection.
Historical Vulnerability Database
Binary Vulnerability Analysis accesses a comprehensive database of over 20,000 historical vulnerabilities. This feature allows users to assess their binary files against a vast array of known issues, ensuring thorough security checks. Utilizing this extensive database enhances users' ability to fortify their applications against potential threats.
Advanced Decompilation Techniques
Leveraging cutting-edge decompilation tools like Ghidra, Binary Vulnerability Analysis transforms binaries into understandable code structures. This key feature allows for better analysis and identification of vulnerabilities, streamlining the security auditing process and providing developers with critical insights to enhance their software's defenses.
You may also like: